One of the toughest CV challenges faced in the cyber security realm is ensuring your credentials stand out in a highly competitive field. Our guide offers tailored strategies that will help you hone your CV to showcase your unique skills and experiences, giving you the edge you need.
- Applying the simplest CV design, so that recruiters can easily understand your expertise, skills, and professional background;
- Ensuring you stand out with your header, summary or objective statement, and a designated skills section;
- Creating your CV experience section - no matter how much expertise you have;
- Using real life professional CV examples to enhance the structure and outline of your profile.
If you still have no muse to write your professional CV, find some more industry-leading examples.
Resume examples for cyber security
By Experience
Mid-Level Cyber Security Consultant
- Structured and Concise Presentation - The CV excels in presenting information clearly and succinctly. Each section is well-organized, making it easy to navigate through the candidate’s career history, education, skills, and achievements without being overwhelmed by unnecessary details.
- Diverse Career Trajectory - Rosie Gray’s career path demonstrates a clear progression from a Junior Security Analyst to a Senior Security Testing Consultant, underscoring her dedication to growth and development in the cybersecurity field. This advancement highlights her increased responsibility and expertise within prominent industry players like BAE Systems and KPMG.
- Technical Proficiency in Cybersecurity - The CV showcases an impressive array of industry-specific skills and qualifications like CREST Registered Tester and OSCP. Furthermore, it demonstrates proficiency in various programming languages and security methodologies, reinforcing her technical depth and relevance to security testing roles.
Senior Cyber Security Engineer
- Career Trajectory Articulating Growth - Ava Phillips' CV effectively maps a solid career progression from a Security Analyst at QinetiQ to a Senior Cyber Security Engineer at BT Group. With each role, there is a clear demonstration of advancement through responsibilities and skill development, particularly in the areas of network troubleshooting, user permissions management, and firewall rule optimization.
- Showcases Technical Proficiency in Industry-Specific Tools - The document highlights Ava's adeptness in using specialized tools like the Atlassian Stack, PostgreSQL, and SIEM tools. This emphasis on technical capability not only underscores her contribution to enhancing security protocols but also her ability to reduce breach incidents and improve server stability through advanced methodologies.
- Leadership and Mentoring Skills Addressed - Phillips' CV places a strong focus on her leadership capabilities, demonstrated by her role as a mentor to junior team members. Her efforts in knowledge transfer and team mentoring have led to a measurable reduction in unresolved issues, showcasing her impact on strengthening team competence and fostering a culture of continuous learning.
Lead Cyber Security Architect
- Logical Flow and Conciseness in Presentation - The CV is structured logically with clearly demarcated sections that are easy to follow. Each experience entry includes impactful bullet points that concisely describe responsibilities and achievements using specific metrics, enhancing clarity and readability.
- Progressive Career Development - Rosie Gray’s career trajectory is highlighted by clear promotions and increasing responsibility. Transitioning from an Information Security Consultant to a Senior Lead Cybersecurity Architect reflects a significant growth path in cybersecurity, showcasing her rising expertise and leadership in the banking sector.
- Emphasis on Technical Prowess - The CV impressively details unique industry-specific elements like threat modeling, cloud computing strategies, and secure code reviews. This highlights a deep technical proficiency that is crucial in cybersecurity roles, emphasizing Rosie's capability to handle intricate technical challenges.
Executive Director of Cyber Security
- Structured Content Presentation - The CV is presented in a structured and concise manner, with clear headings and bullet points that make it easy to digest. This layout effectively highlights key information such as experience, skills, and education, enabling readers to quickly grasp the candidate's qualifications and experience.
- Progressive Career Trajectory - Henry White's career trajectory is impressive, showing a steady progression from IT Strategy Consultant to Senior Director in Cybersecurity Consulting. This indicates a consistent growth in responsibilities and expertise, reflecting his ability to take on more complex roles and deliver impactful results in various positions.
- Industry-Specific Expertise - The CV details Henry's proficiency in industry-specific methodologies and tools such as cloud modernization, digital transformation, threat modeling, and security architecture. These elements underline his technical depth and uniqueness in the cybersecurity consulting space, emphasizing his capability to tackle complex security challenges.
By Role
Cyber Security Analyst
- Structured and Focused Presentation - The CV is well-organized with distinct sections covering experience, education, skills, and achievements, ensuring clarity and easy navigation. Each point is concise, presenting significant data without overwhelming the reader, which highlights the candidate's ability to communicate complex information succinctly.
- Diverse Experience and Growth - Eva Fisher demonstrates a solid career trajectory, advancing from an IT Security Consultant to a Cyber Security Specialist. Her moves reflect upward mobility and expertise gained across different high-profile companies, emphasizing her adaptability and growth in cyber security and risk management.
- Noteworthy Achievements and Impact - The CV speaks volumes about Eva's impact through her initiatives, such as reducing security incidents by 30% and network downtime by 45%. These achievements underscore her capability to drive significant enhancements in service stability and security protocol development, directly contributing to organizational goals.
Cyber Security Consultant
- Attention to Structured Content Presentation - This CV is remarkably clear and well-structured, with each section distinctly segmented and information concisely presented. It efficiently utilizes bullet points for rapid comprehension, ensuring key skills and experiences are highlighted without overwhelming the reader.
- Demonstrates a Proactive Career Development Path - The candidate's career trajectory shows consistent growth and development within the cyber security industry, transitioning from an IT Security Analyst to a Senior Cyber Security Specialist. This progression indicates a dedication to advancing expertise and taking on increasing levels of responsibility.
- Deep Technical Expertise with Industry-Specific Tools - The CV stands out by featuring a robust selection of industry-specific skills and methodologies, such as NIST CVSS, IPTables, and OWASP Top 10. This technical depth underscores the candidate's proficiency in handling complex cyber security challenges.
Cyber Security Engineer
- Strategic Career Advancement Through Diverse Roles - William Hall's career trajectory showcases progressive growth within the cybersecurity domain, beginning as an IT Security Specialist and advancing to a Cyber Security Engineer. This upward movement, combined with the shift from general IT security to more cloud and threat analysis-focused roles, reflects strategic career choices aimed at broadening his expertise and impact in the industry.
- Technical Prowess with Industry-Specific Tools - The CV highlights William's competence with key cybersecurity tools and methodologies. His expertise in advanced email threat prevention, SIEM systems, and developing privileged password management protocols illustrates a deep technical understanding that is essential for modern cybersecurity challenges. Moreover, his certifications, like Azure Security Engineer Associate, underscore his continuous learning and adaptation to evolving technologies.
- Quantifiable Achievements with Real Business Impact - The document effectively emphasizes William's abilities to generate measurable business outcomes through his initiatives. Achievements such as reducing phishing incidents by 40% and enhancing SIEM efficiency by 35% are not mere numbers; they indicate significant improvements in organizational security posture, cost savings, and risk mitigation, demonstrating his capability to deliver strategic and operational value.
Head of Cyber Security
- Structured and Concise Content - The CV is meticulously organized, presenting information in a clear, structured manner, making it easy for the reader to navigate through each section. The summary succinctly captures the candidate’s expertise and achievements, with bullet points highlighting key aspects of their professional journey.
- Impressive Career Growth - The candidate demonstrates significant career growth, progressing from a Cybersecurity Analyst to a Head of Security Operations. This trajectory shows a consistent climb through increasing levels of responsibility and leadership, reflecting their competence and commitment to professional advancement.
- Industry-Specific Expertise - This CV emphasizes a deep understanding of cybersecurity specificities, from threat analysis to incident response and vulnerability management. It highlights proficiency in critical areas such as security operations, network monitoring, and stakeholder management, which are essential for a cybersecurity expert.
Cyber Security Auditor
- Content Presentation and Structure - The CV is meticulously structured with distinct sections for personal information, summary, professional experience, education, skills, courses, achievements, languages, and passions. This clear organization ensures that each aspect of Isabella Watson's qualifications and experience is easy to navigate and understand, highlighting her suitability for roles in cyber security auditing and compliance.
- Career Trajectory and Industry Commitment - Isabella's career demonstrates an impressive trajectory, with her roles evolving from an Information Security Analyst at BT Group to becoming a Cyber Security Auditor at Rolls Royce. This progression showcases a steadfast commitment to the field of cyber security, reflected by her increasing responsibilities and the complex nature of her projects over time.
- Industry-Specific Tools and Methodologies - The CV reflects a strong alignment with critical industry standards and tools such as ISO27001, GDPR, and NIST. Isabella's expertise in implementing these frameworks, alongside her achievements in audit efficiency and third-party compliance, exemplifies her technical depth and understanding of crucial cyber security protocols that are vital for safeguarding organizational security.
Cyber Security Architect
- Content presentation ensures clarity and precision - The CV utilizes a well-structured format with concise bullet points, clearly outlining roles, results, and key skills. Each section is articulated with brevity, allowing for quick navigation through the candidate's career history and achievements.
- Progressive career trajectory with leadership growth - The candidate has moved from an IT Security Analyst to a Security Architect, showing significant career development. This progression is marked by roles in prestigious firms like IBM, Deloitte, and KPMG, indicating a solid industry reputation and expert-level experience.
- Distinct achievements with a focus on business outcomes - The document details numerous achievements where the candidate has made tangible business impacts, such as securing £20M in assets and achieving zero data breaches over three years, highlighting effectiveness and efficiency in cybersecurity roles.
Cyber Security Operations Manager
- Diverse and Solid Career Trajectory - Isla King's CV showcases a well-rounded career in cybersecurity, progressing from a consultant position at IBM to a security operations manager role at BAE Systems. This career progression demonstrates her ability to rise through the ranks by capitalizing on her industry expertise and leadership skills, which is vital for a Cyber Security Operations Lead.
- Strong Array of Soft Skills and Leadership Qualities - The document highlights Isla's proficiency in forming strong stakeholder relationships and leading cross-functional teams. Her success in training programs signifies her capacity to uplift and maintain a qualified team, pertinent to a role that necessitates managing diverse teams and nurturing collaborative environments.
- Noteworthy Achievements and Their Business Impact - The CV details Isla's significant achievements such as a 70% improvement in threat detection capabilities and the implementation of military-grade cyber defense, reducing threats by 40%. These metrics emphasize her contributions to increasing organizational security and operational efficiency, reflecting her effectiveness in delivering impactful cybersecurity solutions.
Cyber Security Risk Manager
- Structured and concise content presentation - The CV is well-organized with clearly defined sections such as Professional Experience, Skills, Education, and Certifications, allowing for easy navigation. Each role is described concisely with bullet points focusing on key responsibilities, making it easy to grasp the candidate's career progression and expertise.
- Dynamic career trajectory showcasing consistent growth - The career path demonstrates an impressive upward momentum with regular promotions and transitions into more responsible roles. Starting as a junior analyst, the candidate moved to managerial positions, highlighting their ability to take on greater responsibilities and evolve within the industry.
- Highlighting adaptability across various industries - The CV reflects the candidate's ability to adapt to different sectors, from technology to healthcare, by applying transferable skills. This cross-industry experience demonstrates versatility and an understanding of diverse market needs, enhancing their attractiveness to potential employers.
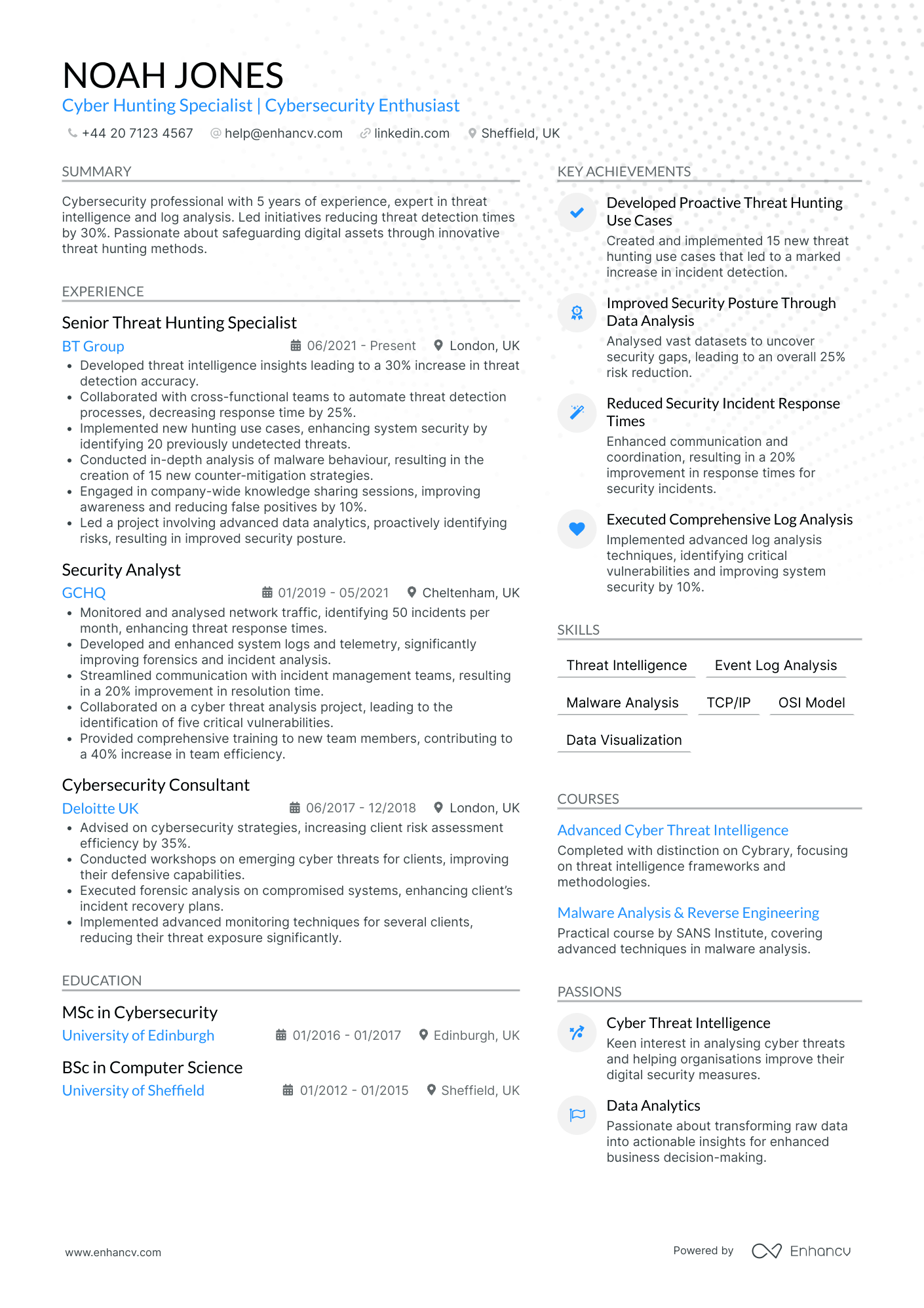
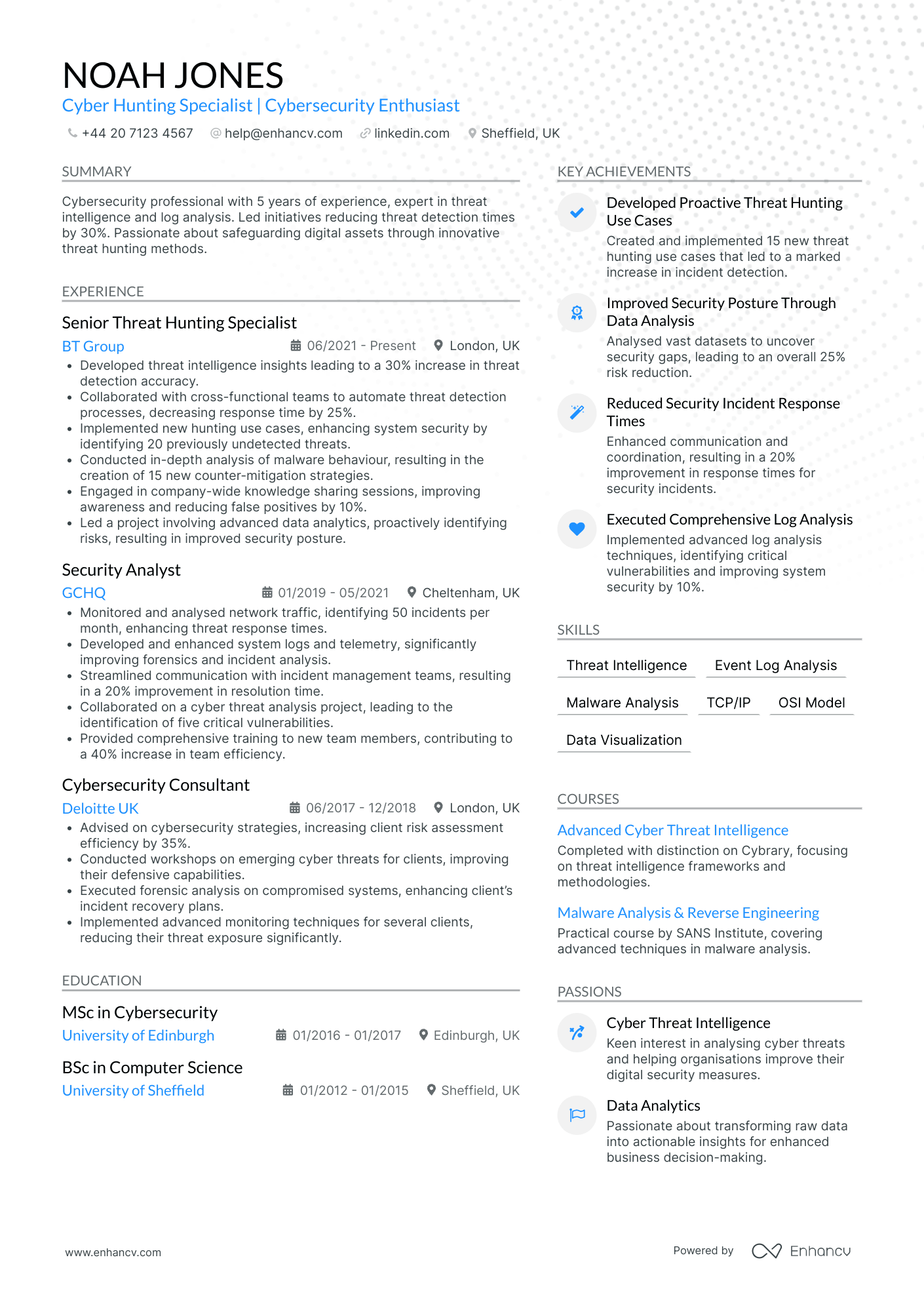
Cyber Security Forensic Expert
- Structured and Concise Presentation - The CV is well-organized, with clear sections that logically progress from personal details to professional experience, education, skills, and other qualifications. This structure aids in highlighting key aspects like achievements and expertise without overwhelming the reader, making the document easy to navigate and understand.
- Clear and Evident Career Growth - Noah Jones' career trajectory shows strong upward mobility, from a Cybersecurity Consultant to a Senior Threat Hunting Specialist. This progression demonstrates not only increased responsibility and expertise but also indicates recognition by employers of his growing capabilities and impact in cybersecurity.
- Impactful Achievements with Business Relevance - The CV emphasizes accomplishments that have meaningful business impacts, such as a 30% increase in threat detection accuracy and a 25% reduction in security incident response times. These achievements underscore the candidate's ability to deliver significant operational improvements, contributing to the enhanced security posture of their organizations.
Cyber Security Software Developer
- Concise and Structured Presentation - The CV stands out due to its well-organized structure and concise presentation. Each section, such as experience, education, and skills, is clearly delineated, making it easy for the reader to quickly assess the candidate’s qualifications. Bullet points are effectively used to summarize achievements and responsibilities succinctly, ensuring important information is highlighted without overwhelming detail.
- Career Growth Across Diverse Roles - The candidate's career trajectory showcases significant growth and adaptability, moving from roles focused on embedded systems engineering to prominent positions in cybersecurity and network protection. This evolution highlights their ability to adjust and progress within rapidly evolving tech industries, reinforcing their commitment to continuous professional development and expertise expansion.
- Achievements with Strong Business Impact - The CV emphasizes accomplishments that convey considerable business value, such as a 30% reduction in security incidents and a 35% improvement in threat detection rates. These achievements not only exhibit technical proficiency but also demonstrate the candidate's ability to drive key performance indicators that contribute substantially to organizational security objectives and operational efficiency.
Cyber Security Incident Responder
- Effective content presentation - The CV excels in clarity and organization, delivering information in a well-structured manner. Each section is clearly defined, with concise bullet points that highlight key details about the candidate's skills, achievements, and career progression, making it easy for readers to grasp essential information quickly.
- Dynamic career trajectory - Sophia Foster demonstrates a progressive career in cyber security, exemplifying growth from an Information Security Specialist to a Senior Cyber Security Incident Responder. Her career advancements reflect solid industry experience and accumulated expertise, with roles that increasingly emphasize leadership and technical sophistication.
- Achievements and business impact - The CV effectively highlights significant achievements, translating them into quantifiable business impacts. Notable successes such as reducing incident management costs by $1M and decreasing response times by 30% underscore her ability to drive cost efficiency and operational improvement, directly benefiting employer performance and resilience.
Cyber Security Project Manager
- Clarity and Structure - The CV is well-organized with clear headings and concise bullet points that make it easy to navigate and quickly grasp essential information. Each section is logically sequenced, contributing to an overall coherent narrative of the candidate's career.
- Career Trajectory and Growth - Sienna West's career showcases a clear upward progression within the cybersecurity management field, transitioning from consultant roles to senior positions like Cyber Security Program Manager. This growth trajectory is highlighted by increased responsibility and scope of impact over the years.
- Achievements and Business Impact - The CV effectively uses quantifiable results to demonstrate the impact of initiatives led by the candidate, such as a 30% reduction in security incidents and a positive audit outcome that ensured regulatory compliance. These demonstrate the candidate's ability not only to meet business objectives but also to drive significant improvements in cybersecurity operations.
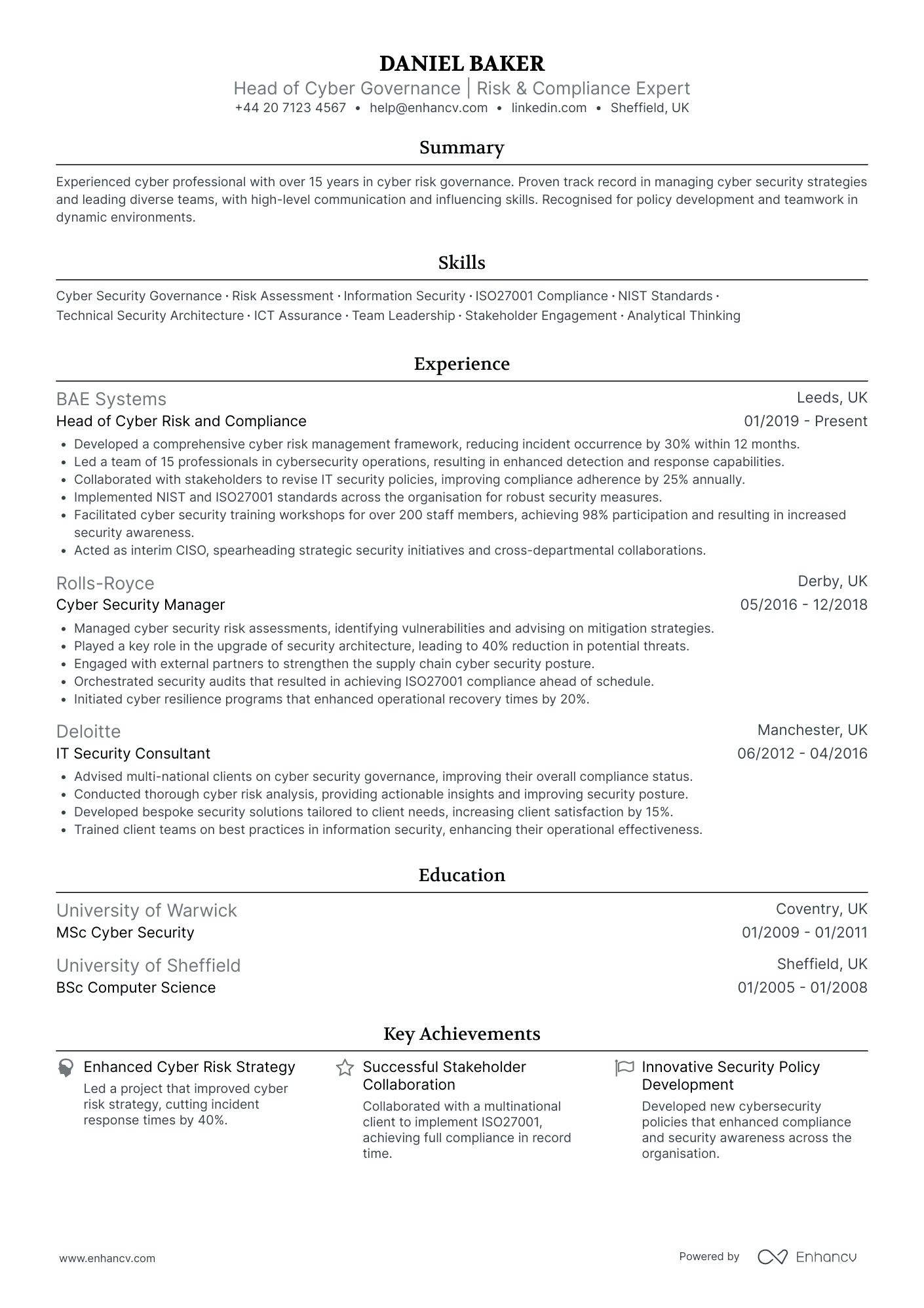
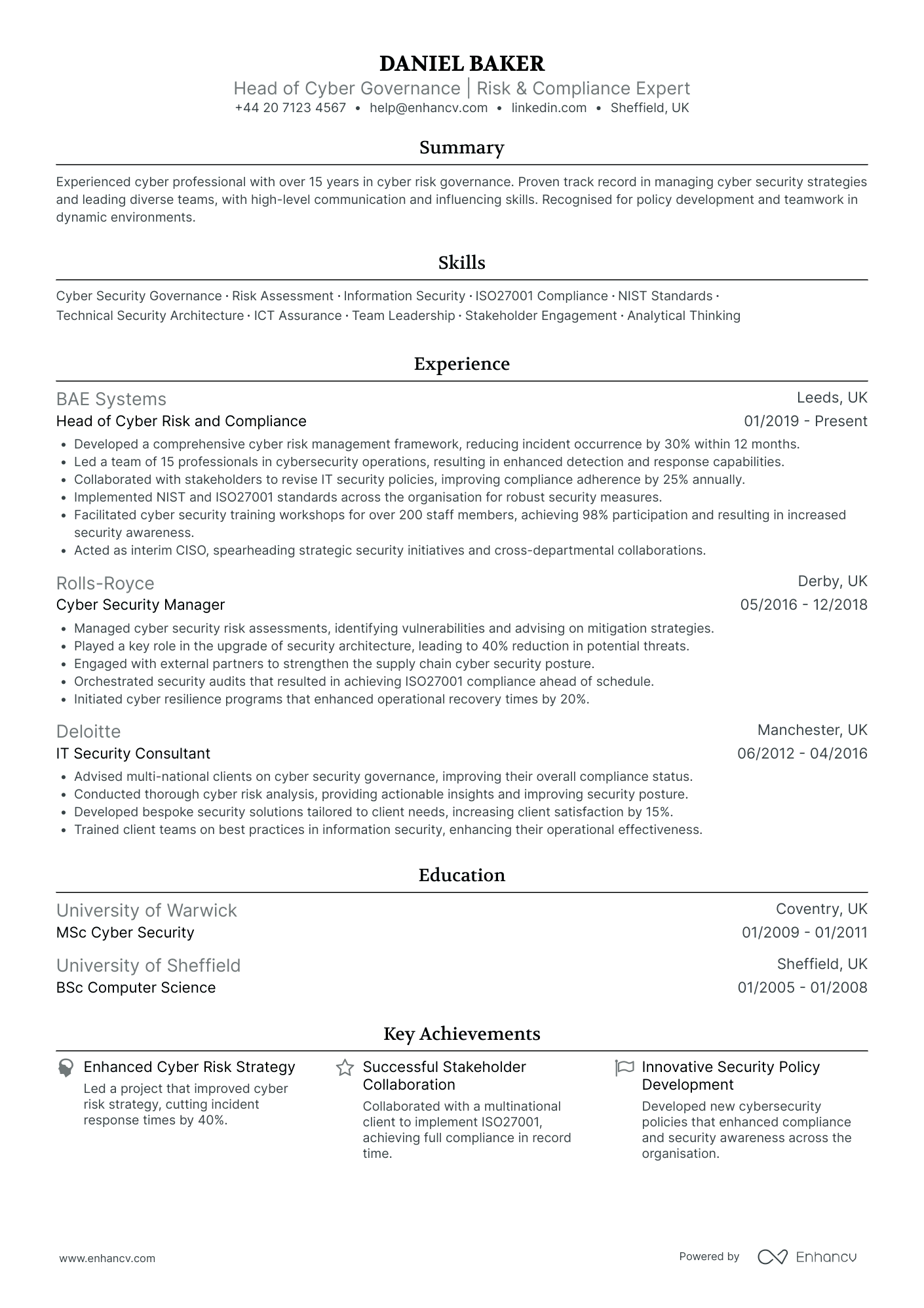
Cyber Security Compliance Officer
- Progressive Career Growth - Daniel Baker's career trajectory showcases a steady progression in roles and responsibilities, advancing from an IT Security Consultant to leading teams as Head of Cyber Risk and Compliance. This indicates not only his technical proficiency but also his ability to manage and grow within the cyber security landscape.
- Comprehensive Skill Set in Cyber Security - The CV highlights Daniel's adeptness in specific cyber security standards and frameworks like ISO27001 and NIST, demonstrating his technical depth and understanding of industry best practices. His ability to implement these standards showcases his expertise in creating robust security measures.
- Impactful Achievements - Particularly notable are the achievements that demonstrate substantial business relevance, such as the development of a cyber risk management framework leading to a 30% reduction in incident occurrence, indicating Daniel's capacity to effectively manage and mitigate security risks.
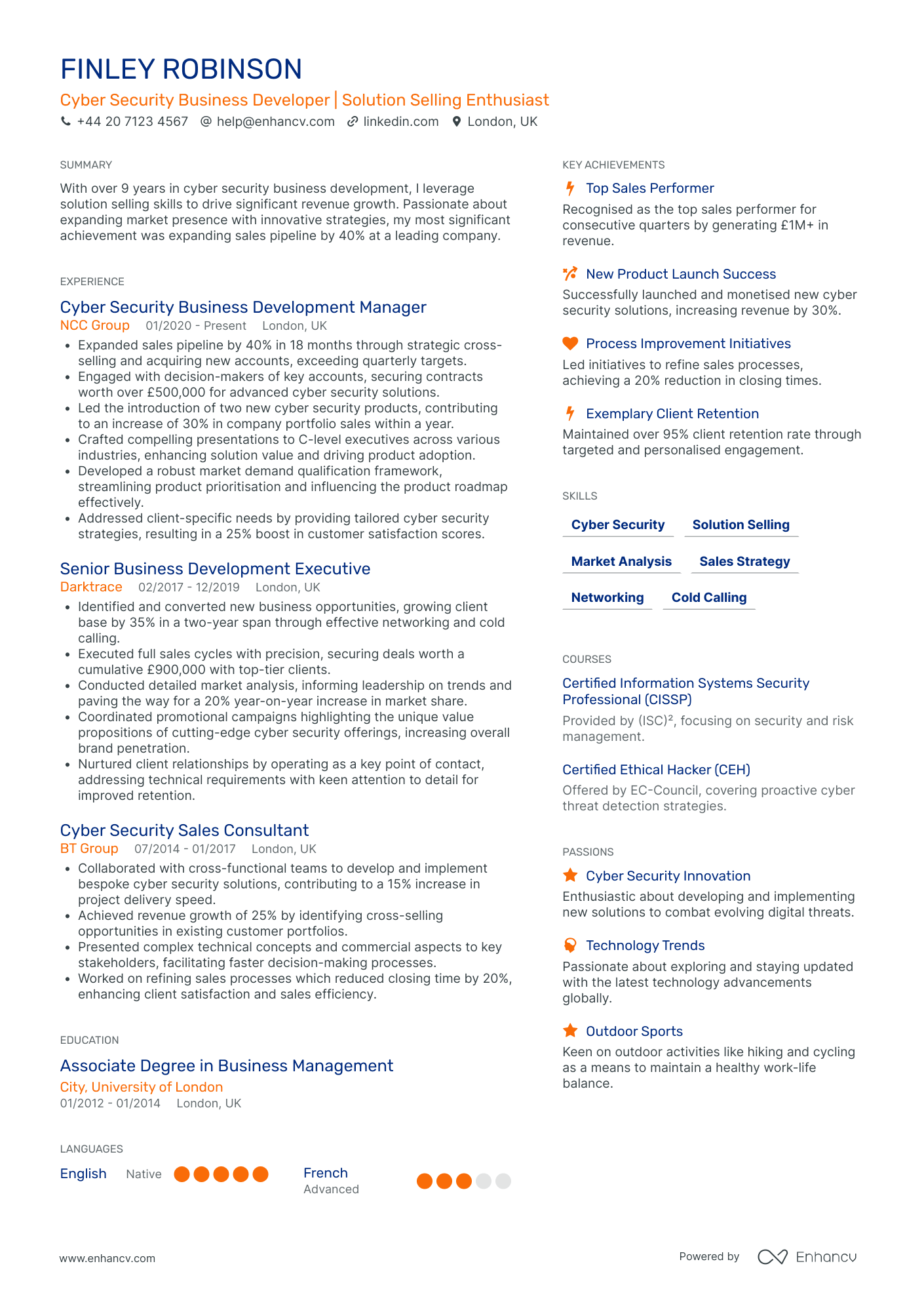
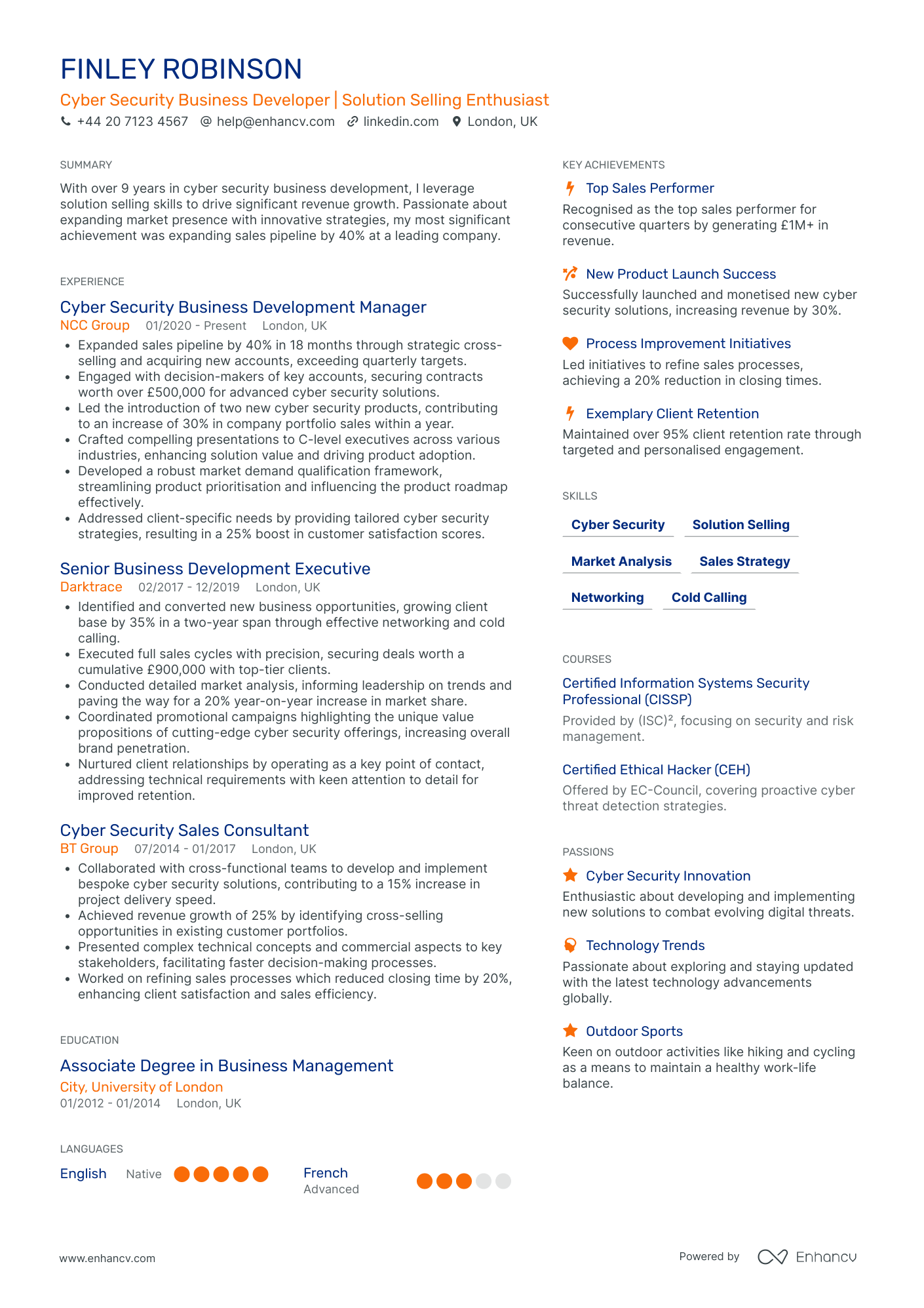
Cyber Security Sales Specialist
- Strategic Presentation and Structure - Finley Robinson's CV is crafted with clarity and structured logically, offering a concise overview of his experiences, skills, and achievements. Each section is clearly delineated, making it easy for potential employers to quickly understand his qualifications and career accomplishments.
- Continuous Career Progression - The CV details a seamless career trajectory characterized by progressive growth within the cybersecurity industry. Finley Robinson has advanced from a Cyber Security Sales Consultant to a Business Development Manager, depicting his capacity for growing alongside industry changes and increased responsibilities.
- Industry-Specific Expertise - This CV highlights Finley Robinson's depth of knowledge in cyber security. His participation in new product launches and certifications such as CISSP and CEH emphasize his commitment to staying at the forefront of industry innovations and methodologies.
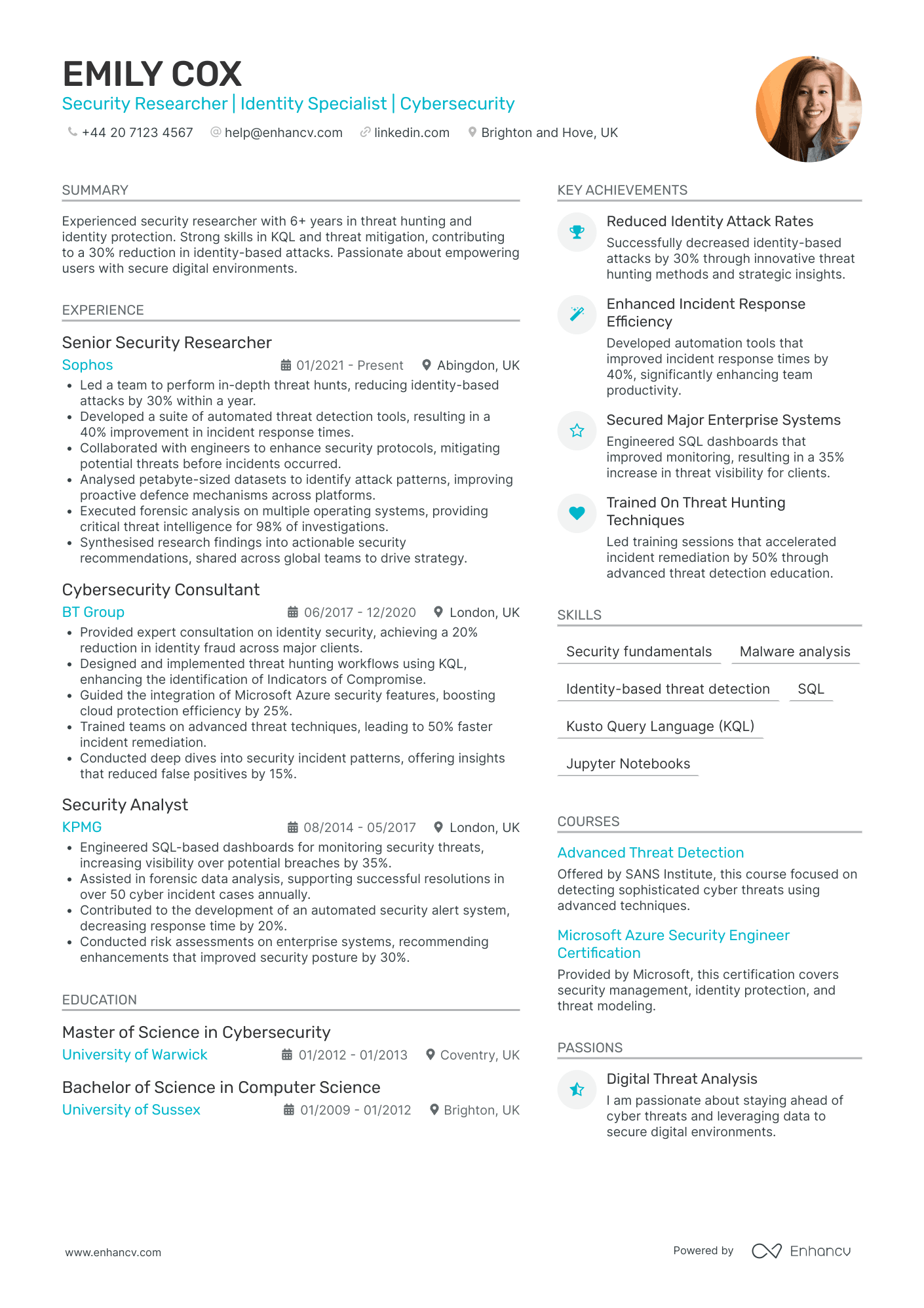
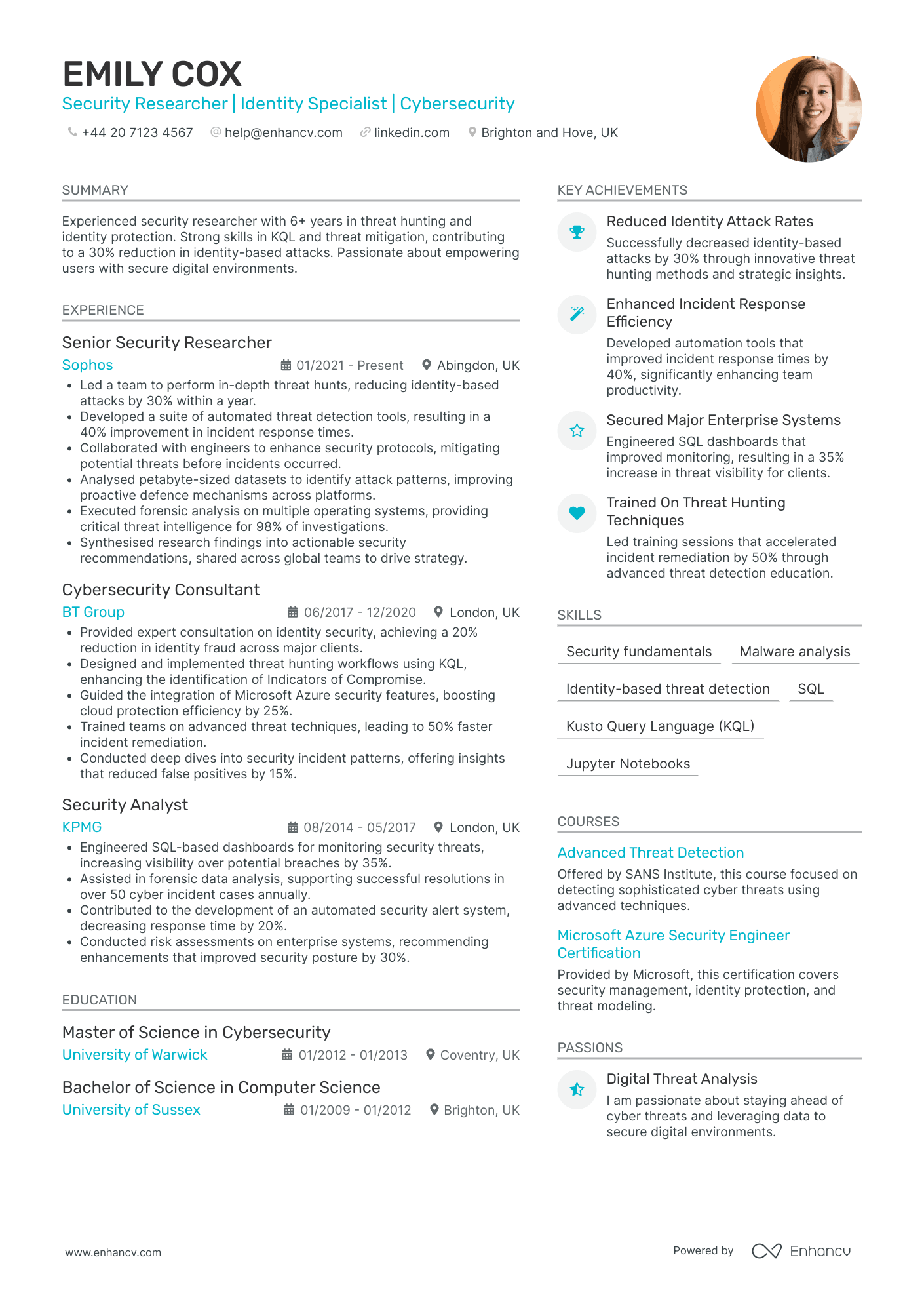
Cyber Security Research Scientist
- Structured Career Progression - Emily Cox's CV displays a clear trajectory of career growth from a Security Analyst to a Senior Security Researcher. With experience in diverse roles and environments like KPMG, BT Group, and Sophos, Emily has steadily advanced, reflecting strong professional development and increasing responsibilities in the cybersecurity sector.
- Technical Expertise and Tool Proficiency - The CV highlights Emily's comprehensive understanding of industry-specific tools and methodologies such as SQL, KQL, and Jupyter Notebooks. These technical capabilities, coupled with her proficiency in digital forensics and identity threat detection, underscore her deep technical knowledge crucial for cybersecurity roles.
- Achievements with Impactful Outcomes - Emily's history of significant achievements, like reducing identity-based attacks by 30% and enhancing incident response efficiency by 40%, demonstrates not just her technical skills but also her ability to achieve substantial results that contribute to organizational security and resilience.
Formatting your cyber security CV to meet the role expectations
Staring at the blank page for hours on end, you still have no idea how you should start your professional cyber security CV. Should you include more colours, two columns, and which sections? What you should remember about your CV format is this - ensure it's minimalistic and doesn't go over the top with fancy fonts and many colours. Instead, focus on writing consistent content that actually answers the job requirements. But, how about the design itself :
- Use the reverse chronological order to showcase your experience, starting with your most recent role;
- Include your contact details (email address, phone number, and location) - and potentially your professional photo - in the header;
- Must-have CV sections include summary or objective, experience, education, and skills: curate the ones that fit your profile;
- Your professional cyber security CV should be between one-to-two pages long: select the longer format if you have more experience.
A little bit more about your actual CV design, ensure you're using:
- plenty of serif or sans serif font (e.g. Montserrat, Exo 2, Volkhov) as they are Applicant Tracker System (ATS) compliant. Avoid the likes of Arial and Times New Roman because most candidates' CVs are in this typography.
When submitting your CV, are you still not sure what format it should be? Despite the myth that has been circling around, most modern ATS systems are perfectly capable of reading PDFs. This format is an excellent choice as it keeps all of your information intact.
PRO TIP
Use bold or italics sparingly to draw attention to key points, such as job titles, company names, or significant achievements. Overusing these formatting options can dilute their impact.
The top sections on a cyber security CV
- Professional Summary showcases your cyber security expertise and goals.
- Core Competencies section highlights specific cybersecurity skills and tools.
- Professional Experience details relevant roles and accomplishments in cybersecurity.
- Education & Certifications lists degrees and relevant cyber security certifications.
- Cybersecurity Projects demonstrate practical experience with real-world applications.
What recruiters value on your CV:
- Highlight relevant certifications such as CISSP, CISM, CEH, and OSCP, as these demonstrate a professional commitment to the cybersecurity industry and its best practices.
- Detail your experience in specific security technologies, frameworks, and regulations like firewalls, SIEM, IDS/IPS, ISO 27001, and GDPR, to show your practical expertise and understanding of compliance requirements.
- Emphasise your hands-on experience with vulnerability assessment and penetration testing, including the methodologies and tools used, to indicate your ability to identify and mitigate security risks.
- Include a section on your soft skills like problem-solving, teamwork, and communication, which are crucial for effectively collaborating with IT teams and explaining security concepts to non-technical stakeholders.
- Showcase a portfolio of projects or contributions to open-source security tools, if applicable, to demonstrate a track record of practical application of your cyber security skills and continuous learning.
Recommended reads:
Our checklist for the must-have information in your cyber security CV header
Right at the very top of your cyber security CV is where you'd find the header section or the space for your contact details, headline, and professional photo. Wondering how to present your the name of the city you live in and the country abbreviation as your address;
- are tailored to the role you're applying for by integrating key job skills and requirements;
- showcase what your unique value is, most often in the form of your most noteworthy accomplishment;
- select your relevant qualifications, skills, or current role to pass the Applicant Tracker System (ATS) assessment. Still not sure how to write your CV headline? Our examples below showcase best practices on creating effective headlines:
Examples of good CV headlines for cyber security:
- Cyber Security Analyst | Threat Intelligence Specialist | CEH Certified | 3+ Years of Experience
- Information Security Manager | Governance, Risk & Compliance Expert | CISSP | 10 Years Progressive Experience
- Network Security Engineer | Firewall and IDS/IPS Solutions | CCNA Security | 5-Year Track Record
- Chief Information Security Officer | Strategic Cybersecurity Leadership | GDPR Proficiency | 15+ Years at Forefront
- Penetration Tester | Ethical Hacking Enthusiast | OSCP | Proven Record over 4 Years
- IT Security Consultant | Cyber Resilience Strategies | ISO 27001 Lead Auditor | 7 Years Dedicated Experience
Your cyber security CV introduction: selecting between a summary and an objective
cyber security candidates often wonder how to start writing their resumes. More specifically, how exactly can they use their opening statements to build a connection with recruiters, showcase their relevant skills, and spotlight job alignment. A tricky situation, we know. When crafting you cyber security CV select between:
- A summary - to show an overview of your career so far, including your most significant achievements.
- An objective - to show a conscise overview of your career dreams and aspirations.
Find out more examples and ultimately, decide which type of opening statement will fit your profile in the next section of our guide:
CV summaries for a cyber security job:
- With a robust 10-year track record in the dynamic field of cyber security, I bring to the table deep expertise in intrusion detection, cryptography, and incident response management. My career is highlighted by a pivotal role in thwarting a significant DDoS attack on a major financial institution, bolstering their defence systems by 300%.
- As an accomplished data analyst transitioning into cyber security, I have sharpened my skills in data encryption and network security over the last three years. Leveraging my analytical prowess and dedication to security principles, I have successfully formulated a predictive analytics model that identified potential breaches, reducing vulnerabilities by 40%.
- Crossing over from a 5-year journey in software development into cyber security, I am equipped with a profound understanding of secure coding practices, application security protocols, and threat modelling. My greatest triumph lies in the redesign of my previous employer’s software security, cutting down the risk of attacks by half.
- Focused and analytical, with a 15-year tenure in the realm of cyber security and a deep-seated expertise in regulatory compliance and ethical hacking. I was instrumental in architecting a novel encryption algorithm that became the cornerstone of secure transactions for a multinational banking corporation, significantly elevating their security stance against cyber threats.
- Eager to synthesise my enthusiasm for technology with a steadfast commitment to security, I seek an entry-level position to develop and apply my skills in risk assessment and mitigation. With a recent degree in Information Technology and dedicated coursework in cyber security principles, I aspire to make impactful contributions to safeguarding digital assets.
- As a recent graduate with foundational knowledge in network architecture and cyber security frameworks, my objective is to grow within the cyber security discipline. My internship experience with hands-on defence simulations has fuelled my desire to pursue a career where I can proactively address and neutralise emerging cyber threats.
How to meet job requirements with your cyber security CV experience
We've now reached the essence of your actual CV - your experience section. This is the space where you can list your career roles and on-the-job successes. Many candidates tend to underestimate just how much time and effort they should put into writing this CV section. Your experience shouldn't be a random list of your responsibilities, but instead:
- Match the job description with your skills, values, and accomplishments;
- Start each bullet with a strong action verb, followed up with one key skill and your outcome of applying this skill;
- Spotlight parts of your career history that are relevant to the job you're applying for.
Before we move on, make sure to check out some professional CV experience sections.
Best practices for your CV's work experience section
- Implemented a company-wide anti-phishing campaign, reducing phishing success rates by 65% within the first year and enhancing overall security awareness among employees.
- Developed and enforced security policies compliant with GDPR, leading to zero non-compliance incidents and safeguarding customer data privacy.
- Performed regular security audits and vulnerability assessments, identifying and mitigating risks in a timely manner to maintain business continuity and system integrity.
- Designed and managed the installation of an IDS/IPS system, which detected and prevented over a thousand intrusion attempts in the first quarter post-deployment.
- Collaborated with cross-functional teams to integrate security practices within the software development lifecycle, resulting in a 40% decrease in security-related bugs in released software.
- Managed incident response activities for security breaches, minimising damage, conducting thorough investigations, and providing comprehensive post-mortem reports that improved response protocols.
- Maintained up-to-date knowledge of emerging security threats and implemented proactive defences to protect organisational assets and sensitive data.
- Conducted regular security training sessions for new hires and existing staff, fostering a culture of security-mindedness across all departments.
- Contributed to the selection and deployment of a multi-factor authentication system, significantly reducing the risk of unauthorised access to sensitive systems and data.
- Developed and implemented an advanced threat detection system that reduced false positives by 35% and improved threat response times by 50%.
- Managed a team of 5 security analysts to monitor network traffic and investigate suspicious activity, cutting breach detection time by 40%.
- Coordinated with cross-functional teams to execute a company-wide security training program, elevating employee compliance with security protocols by 75%.
- Oversaw the transition to a cloud-based security infrastructure, enhancing system scalability and reducing operational costs by 20%.
- Authored the company’s incident response playbook, which streamlined the process and improved reaction speed to incidents by 30%.
- Conducted quarterly security audits, identifying critical vulnerabilities and making recommendations that led to a 25% overall increase in system security.
- Advised Fortune 500 clients on cybersecurity best practices, leading to an average 20% uplift in their security posture.
- Implemented a robust security framework for a financial services client, resulting in the prevention of potential annual losses estimated at $10M.
- Spearheaded a data encryption project for a healthcare client, ensuring compliance with HIPAA regulations and safeguarding patient information.
- Designed and installed a secure network architecture for a new data center, increasing data throughput by 60% while maintaining compliance with industry standards.
- Led the initiative to upgrade security protocols, which resulted in the elimination of outdated systems and a 35% reduction in maintenance costs.
- Collaborated with software developers to incorporate security measures in the early stages of application design, reducing potential vulnerabilities by 80%.
- Monitored for emerging threats and conducted in-depth analysis, contributing to a 20% decrease in successful phishing attacks.
- Automated regular system backups and failover processes, minimizing downtime in the event of a cyber incident and ensuring business continuity.
- Co-developed a proprietary risk assessment tool that increased the efficiency and accuracy of security audits by 30%.
- Implemented a comprehensive endpoint security solution, reducing malware infections by 90% across the organization.
- Managed the deployment of security patches for enterprise systems, mitigating the risk of exploitation of known vulnerabilities.
- Conducted regular penetration tests, identifying and remedying security issues before they could be exploited by external threats.
How to ensure your cyber security CV stands out when you have no experience
This part of our step-by-step guide will help you substitute your experience section by helping you spotlight your skill set. First off, your ability to land your first job will depend on the time you take to assess precisely how you match the job requirements. Whether that's via your relevant education and courses, skill set, or any potential extracurricular activities. Next:
- Systematise your CV so that it spotlights your most relevant experience (whether that's your education or volunteer work) towards the top;
- Focus recruiters' attention to your transferrable skill set and in particular how your personality would be the perfect fit for the role;
- Consider how your current background has helped you build your technological understanding - whether you've created projects in your free time or as part of your uni degree;
- Ensure you've expanded on your teamwork capabilities with any relevant internships, part-time roles, or projects you've participated in the past.
Recommended reads:
PRO TIP
Talk about any positive changes you helped bring about in your previous jobs, like improving a process or helping increase efficiency.
The CV skills' divide: between hard and soft skills
Of course, you may have read the job requirements plenty of times now, but it's key to note that there is a difference between technical and personal skills. Both are equally relevant to your job application. When writing about your skill set, ensure you've copy-pasted the precise skill from the job requirement. This would not only help you ensure you have the correct spelling, but also pass any Applicant Tracker System (ATS) assessments.
- Hard skills show your technological capabilities. Or whether you'll be a good technical fit to the organisation. Ensure you've spotlighted your hard skills in various sections of your CV (e.g. skills section, projects, experience) by including the technology and what you've attained;
- Soft skills pinpoint your personality and people or communication skills, hinting at if you'll easily accomodate into the team or organisation. Quantify your soft skills in your CV achievements, strengths, summary/objective, and experience sections. Always support your soft skills with how they've helped you grow as a professional.
Top skills for your cyber security CV:
Network security
Intrusion detection
Security Information and Event Management (SIEM)
Firewall administration
Penetration testing
Vulnerability assessment
Cryptography
Incident response
Secure coding practices
Risk management
Analytical thinking
Problem-solving
Attention to detail
Communication
Adaptability
Teamwork
Time management
Ethical judgement
Continuous learning
Stress tolerance
PRO TIP
Focus on describing skills in the context of the outcomes they’ve helped you achieve, linking them directly to tangible results or successes in your career.
Education and more professional qualifications to include in your cyber security CV
If you want to showcase to recruiters that you're further qualified for the role, ensure you've included your relevant university diplomas. Within your education section:
- Describe your degree with your university name(-s) and start-graduation dates;
- List any awards you've received, if you deem they would be impressive or are relevant to the industry;
- Include your projects and publications, if you need to further showcase how you've used your technical know-how;
- Avoid listing your A-level marks, as your potential employers care to learn more about your university background.
Apart from your higher education, ensure that you've curated your relevant certificates or courses by listing the:
- name of the certificate or course;
- name of the institution within which you received your training;
- the date(-s) when you obtained your accreditation.
In the next section, discover some of the most relevant certificates for your cyber security CV:
PRO TIP
Use mini case studies or success stories in your CV to demonstrate how your skills have positively impacted previous roles or projects.
Recommended reads:
Key takeaways
Impressing recruiters with your experience, skill set, and values starts with your professional cyber security CV. Write concisely and always aim to answer job requirements with what you've achieved; furthermore:
- Select a simple design that complements your experience and ensures your profile is presentable;
- Include an opening statement that either spotlights your key achievements (summary) or showcases your career ambitions (objective);
- Curate your experience bullets, so that each one commences with a strong, action verb and is followed up by your skill and accomplishment;
- List your hard and soft skills all across different sections of your CV to ensure your application meets the requirements;
- Dedicate space to your relevant higher education diplomas and your certificates to show recruiters you have the necessary industry background.